Why is the digitization of industrial networks one of the key challenges for cybersecurity?
The industrial revolution 4.0 is taking production and related industries into a new era. Production needs are strongly dependent on data, both delivered and triggered in real time. Technologies such as robotics and automation rely on data and advanced data analysis. Intelligent Industry 4.0 machines are connected. This connection allows you to capture, share, analyze and use data to optimize industrial systems by combining IT and OT.
Operational technology (OT) – as defined by Gartner, is hardware and software that detects or causes change by directly monitoring and/or controlling physical devices, processes and events in an enterprise. By comparison, information technology (IT) is used to control the sharing, collaboration and use of data through applications, servers, endpoints, etc. OT is common in industrial control systems (ICS) such as SCADA systems. In the world of critical infrastructure, OT can be used to control power plants or public transport.
With the development of this technology and convergence with networking technology, the demand for OT security grows exponentially. It is worth mentioning here that the security of industrial systems has many features in common with IT security. For example, confidentiality, integrity and availability (CIA) are the attributes of information that create logical foundations for all categories of cybersecurity products – IT and OT.
In the OT area, their prioritization is as follows:
- Availability: Issue # 1 for all operators and a potentially critical health and safety issue.
- Integrity: How to protect the target system from unauthorized changes.
- Confidentiality: how to protect system details from unauthorized access and misuse.
As you can see above, OT security is all about the data being available first of all, then unchanged, and only finally not accessible to unauthorized persons. Comparing IT security with OT security, we see fundamental differences in the approach to architecture. So far, the model cybersecurity concept for OT has been isolated investments, galvanically separated from the Internet and properly categorized within the critical infrastructure.
Examples of OT infrastructure:
- PLC’s – Programmable Logic Controllers – programmable logic controllers are computers that control the parameters of systems, e.g. production systems.
- SCADA – Supervisory Control And Data Acquisition – control system architecture consisting of computers, network data transmission and graphic user interfaces (GUI) for high-level process management, as well as other peripheral devices such as programmable logic controllers (PLC) and controllers PID (discrete proportional-integral-derivative) for connection to a process plant or machines.
- DCS – Distributed Control Systems – A computerized control system for a process or plant, typically with multiple control loops, in which autonomous controllers are distributed throughout the system, but there is no central supervisory control for an operator. The DCS concept increases reliability and lowers installation costs by locating the control functions close to the processing plant, remote monitoring and supervision.
Since OT systems support key installations, in our article we will use an example of a system that supplies a substance that is crucial for human life – water.
Waterline attacks are not new – from cutting off the water during a medieval castle siege to apocalyptic scenes from science fiction movies.
Water systems are vulnerable for several general reasons:
- They are defined in terms of a geographic location – they have strict boundaries, and while pollution may spread to adjacent areas to ease it, it does so more slowly.
- Built-in disaster protection in terms of extraneous detection, filtering and redundancy, which can help in the event of a cyber attack, but can also alert attacker on what to be cautious about
- Physical access is no longer a deterrent due to the lack of separation, the sewer management system network is accessible from multiple points, including remote interception.
However, they undoubtedly also have aspects that can be the starting point for understanding how to protect OT infrastructure.
Let’s look at the basic steps used to ensure the safety and cleanliness of water in sewage systems:
- Monitoring the inputs of the water source itself, incoming treatment media, wastewater or treated wastewater that is fed into the system.
- Monitoring of “water product” outputs to the various supply circuits, tanks and pumps.
- A signaling system and a set of alert procedures help avoid victims resulting from a lack of awareness of the dangerous conditions.
The above monitoring techniques naturally fit into three risk categories (non-random sequence):
- availability in the simplest case makes sense (something is not read) to make sure that a safe product comes out of the tap,
- integrity is about ensuring that process control is not tampered with without authorization,
- confidentiality means ensuring that input data are complied with as required and expected.
Marty Edwards, Director of Strategic Initiatives at the Institute of Advanced Studies – a recognized security specialist, OT points out that the speed of information provision is crucial “A security solution that does not keep up with the pace of activities is not only of little use; this is a net loss for the enterprise. Operators grapple with alert noise and exception loops, and waste a lot of time before taking action. “
Because the plant operators’ mindset is to prioritize maintaining availability and business continuity. In many cases, ICS cybersecurity solutions pose the problem of availability: they perform passive activities, generate many secret alerts, and allow you to analyze endless backlogs.
Even if the alerts were correct, the priority would be to restore the installation operation, not to analyze the root causes of the security incident.
The MITRE ATT&CK framework distinguishes several key OT risk areas within the ICS priority framework for availability, integrity and confidential.
The eleven outcomes of ICS attacks identified under MITER ICS ATT & CK affect key information attributes as follows:
- Availability Impact: Includes activities that result in loss of control, loss of view, property damage, denial of control, denied panel view, loss of availability, loss of productivity and revenue and, of course, loss of security.
- Impacts on Integrity: Include actions that result in control manipulation and view manipulation.
- Impact on confidentiality: includes activities that lead to the theft of operational information.
Table 1. Analysis of OT risk areas broken down by severity levels (Purdue 1-5):
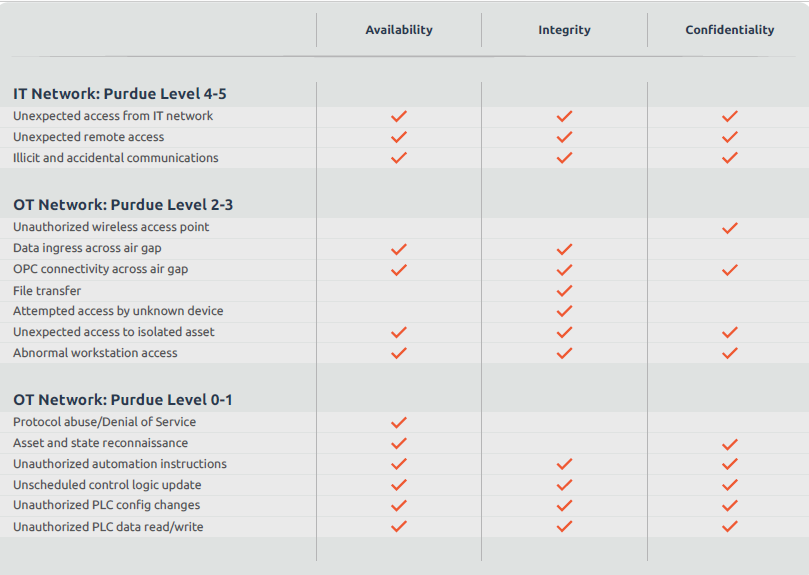
OT security has long ceased to be guaranteed by galvanic separation from the IT network, as can be seen in the above table, the most harmful threats are those originating in the IT network. Nevertheless, it is the OT network that is most often the “entry point”.
Therefore, below we present the key technologies that currently constitute an appropriate line of defense for OT infrastructure
Industrial Firewall/IPS is a physical device, implemented in transparent-bridge mode (for seamless integration and uninterrupted operation of OT systems), that sits in front of critical media surveillance endpoints, protecting PLCs, VFDs, and other networked devices. Learns and enforces normal operations in the plant environment and actively eliminates threats to OT in real time. The firewall should protect the ICS network against:
- unauthorized configuration changes,
- device resets, device readings
- logic updates and value messages.
Due to the extreme sensitivity of data flows, the rules are constructed based on the learned traffic patterns encountered in the protected environment and take into account the number of unique possibilities within various internal control systems protocols and communication environments (the last fragment is not read somehow). For products operating in an OT environment to be truly useful, they must understand operational ranges of values, e.g. this threshold or out-of-range violations are detected and appropriately handled based on the needs of each person in the customer environment.
Typically, this is the last line of defense to protect your establishment’s assets from unauthorized or unintended (misuse) use.
The Data Diode creates a sealed tunnel (airgap) that controls, restricts and enables communication from sensitive, proprietary parts of the OT network. It provides an isolated, one-way data transfer in such a way that no network information is exposed. The diode creates full isolation between protocols, between two network units, and thus transmits data without exposing it to an untrusted network and provides protection against unauthorized communication.
The key benefits of the implementation are:
- Acceptance and protection of data transfer only one way thanks to optical isolation.
- Control of various protocols and data types – both OT and IT.
- Possibility of multi-level validation of your OT flows: original file structure, AV signatures, DLP sensitive data and heuristic analysis.
- Consolidation of Standard Operational Syslog, binary audit, and data transfer logging security events.
Industrial Access – OT did not resist the digital evolution, now remote access is necessary and often included in the SLAs of manufacturers of OT network communication solutions. OT remote access solutions are more precise than any VPN thanks to the ability to control access based on policies configured according to:
- Protocol
- Activities
- Type of user
The rules should be constantly enforced during the access session to provide an option for remote workers or external vendors to access endpoints on the OT network – without the network vulnerable to attack. Due to necessity of remote access this solution can be seen as critical.
In summary, Operational Technology (OT) is used to control physical systems such as those found in production. It also includes industrial control systems (ICS) and ICS management systems, as well as supervisory control and data acquisition systems (SCADA). The July 2020 alert With the NSA and CISA (Cybersecurity and Infrastructure Agency) sums up a serious OT security problem, pointing to OT-IT convergence. The report states that “all DoD, NSS, DIB and US critical infrastructure facilities should take immediate action to secure their OT assets. “
By combining OT and IT technologies, the previously isolated and protected systems used by manufacturing are now open to the same types of security threats that typically attack IT systems. This includes ransomware attacks and distributed denial of service (DDoS). The reality of connecting IT with OT is described in the IBM X-Force “Threat Intelligence Report Index 2020”. The results of the report show a huge, 2,000% increase in the number of cyber incidents affecting OT infrastructure. The report also highlights the increasingly destructive nature of these attacks – ransomware attacks against OT environments increased by 67% in 2019.
To learn more about the practice of securing OT systems, please read:
Bayshore Networks – INFORMATION SECURITY AND A PRACTICAL APPROACH TO THE DEFENSE OF WATER SYSTEMS
And contact our specialists to discuss your findings!




