What is MITRE ATT&CK
In 2013, the non-profit organization MITRE introduced to the IT world the proprietary framework called ATT&CK – Adversarial Tactics, Techniques & Common Knowledge – as a way of describing and categorizing the enemy’s behavior in cyberspace. ATT&CK is an ordered list of known attackers’ behaviors, which have been compiled into tactics and techniques and expressed in several matrices as well as via STIX/TAXII (including a separate article – link). It is based on comprehensive observations and analysis of data on the behavior of attackers when hacking a network, and is therefore now widely used to measure defensive capabilities, create incident response scenarios, and estimate return on investment in cybersecurity technologies (Return on Security Investment – ROSI).
MITRE ATT&CK has been divided into several different matrices – Enterprise, Mobile and PRE-ATT&CK. Each of these matrices contains different tactics and techniques related to the subject of that matrix.
| Enterprise | Mobile | PRE-ATT&CK |
| Techniques and tactics used to exploit Windows, Linux and MacOS. | Techniques and tactics used to exploit mobile devices | Techniques and tactics connected to pre-attack activities of an attacker |
In each of the categories presented above, “tactics and techniques” are listed. What exactly do they mean?
- Tactics – what the attacker wants to achieve with a given behavior.
- Techniques – how the attacker wants to achieve it, techniques are specific methods / behaviors.
For example – the tactic is to obtain access data to the account, the technique – brute force. Following on from our example, an attacker may want to access the network and install spyware on as many computers and servers as possible on the network.
In order to be successful, he must successfully complete several intermediate steps:
- First, get access to the internal network – whether via a phishing link, an automatic script hidden on a website or malware passed to a pendrive.
- Then get the right type of access – it can be done by exploiting system vulnerabilities, or by using the identity of the hijacked computer.
- After obtaining the appropriate data, the attacker may install spyware or continue exploiting vulnerabilities and spreading internally until the target systems are infected.
- Regardless of the complexity of the third level – if the organization does not have the appropriate staff and technology – the attacker will achieve his target.
For deep dive into T&T, please visit: https://attack.mitre.org/matrices/enterprise/
However, before any attempt to access the network occurs, the attacker collects information about the target – this phase is covered by the PRE-ATT&CK matrix. The tactics and techniques described in the framework are loosely related to Lockheed Martin’s CyberKill Chain:
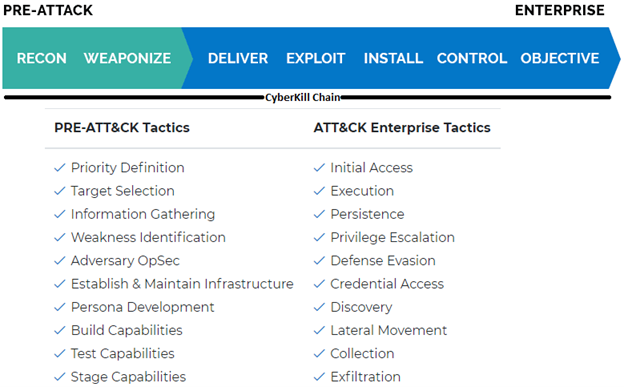
Any defensive actions that relate to attackers and their behavior can benefit from the ATT&CK taxonomy. In addition to providing a common wording for cybersecurity professionals, ATT&CK also provides the basis for the development of scenarios for pentests and Red Teams excercises. This gives blues and reds a common language in relation to the opponent’s behavior.
Examples where the use of the ATT&CK taxonomy may be useful:
- Purchase, implementation and configuration of cybersecurity technologies: ATT&CK’s tactics and techniques are a source of information on points to be monitored to detect and neutralize attackers.
- Proactive threat detection: The ATT&CK activity chain analysis allows analysts to recognize “blind spots” in their current infrastructure and take them into account to respond to incidents faster.
- Strategic Cybersecurity Analysis: The Security Operations Center (SOC) and incident response team can refer to the techniques and tactics described in ATT&CK to understand:
- where are the strengths and weaknesses of the defense,
- how to adjust existing detection and remediation mechanisms,
- what misconfigurations and other operational problems may exist,
- what to focus on pentests or Red Team excercises.
4.Recognition of attackers: Actors and groups may be associated with specific, defined behavior “typical” for them.
5. Tool integrations: Various tools and services can standardize ATT&CK’s tactics and techniques, bringing consistency to defense.
6. Clear Communication: By sharing information about an attack, actor or group, or measures of control, defenders can ensure coordination using a common language of ATT&CK techniques and tactics.
MITRE ATT&CK is a single pane of insight into the known details of criminals’ behavior in cyberspace. Knowing and understanding the framework is one of the main weapons in the arsenal of a cybersecurity analyst – it allows you to correlate facts faster, and even predict the behavior of aggressors and coordinate efficient defense processes.
Currently, attackers are looking for ways like social engineering to avoid detection by traditional security tools – this requires a change in the approach to detection and defense. ATT&CK takes our perception from low-level indicators such as IP addresses and domain names and causes us to look at attackers and our defenses through the prism of behavior. However, this new perception does not mean automatic success. The path to behavior detection and prevention is much more difficult than the old deploy-and-forget tools. In addition to the huge amount of already known behaviors, attackers develop new ones every day. Therefore, the development of MITRE is a common responsibility of the cybersecurity world to continue to defend enterprises.




