TRELLIX ABOUT LOG4J
We recently reported the merger of McAfee and FireEye into Trellix. It hasjust released its first threat report – topped by the Log4j vulnerability, known as CVE-2021-44228, which has dominated not only the headlines but also the attention of defenders and corporate security teams. There is a reason for this – it is the most serious vulnerability detected in at least the last decade.
What Trellix recommends to mitigate the risk of Log4j library vulnerability?
Log4j Java library from trusted Apache organization – is used in products such as Apple iCloud, Steam, Samsung Cloud Storage and many others. This is why the problem is so serious – the risk applies to every product that has integrated Log4j with its applications and websites.
Exploiting this vulnerability allows an attacker to force a vulnerable website or application to load and execute malicious Java code from an untrusted remote location. Attack vectors vary, but the most common one involves the attacker sending crafted strings as part of the network protocol to the target machine, such as a modified HTTP header sent as part of a POST request.
Below you can see attack schema:
Step 1 – the attacker sends a specially crafted string to the web server where the affected application resides. The string can be obfuscated to bypass network signatures
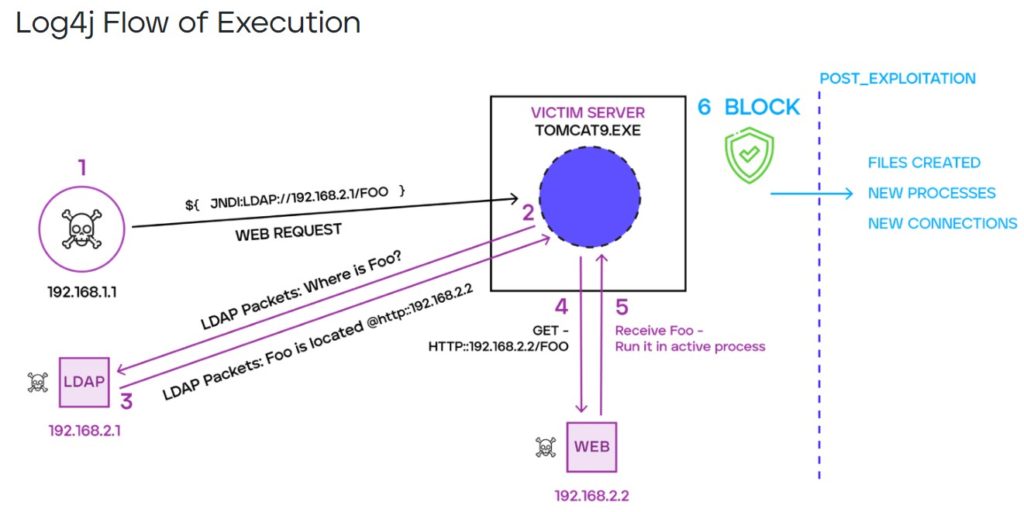
Step 2 – The application proceeds to decrypt this string in order to load it into memory. After loading into memory, the application initiates an LDAP connection to request the address of the location of the malicious code.
Step 3 – The attacker’s controlled LDAP server replies with the location of the malicious Class file, pointing to the HTTP URL of the location where it is hosted.
Step 4 – The vulnerable application initiates the download of a malicious file.
Step 5 – The vulnerable application will load and run the malicious file from step 4.
Risk mitigation – what apart from uploading patches?
Good prevention is to run a periodic memory scan to detect the presence of a malicious code file. There is a high probability of finding the decrypted string used at that time in the process’s memory. If the memory is scanned after downloading a malicious class file, this content will also be available for scanning in decrypted form. Naturally, the risk is what if the code has already been executed and, for example, a connection has been established.
It is worth mentioning that CISA.gov provides the Log4j scanner to help organizations identify potentially vulnerable Internet services affected by the Log4j vulnerabilities
Another way is through expert rules developed by Trellix experts
Expert rules are configurable access control rules that end users use to detect suspicious activity not commonly observed by other scanners. Trellix also share community expert rules mapped to the MITRE ATT&CK matrix through their public GitHub.
These capabilities allow you to target Log4j-prone applications and identify the point at which they are used. Here are some of the tools that can be used:
However, to fully protect the environment against network-vector attacks such as Log4j, a layered, strategy of network security combined with targeted endpoint memory scans is essential.As a team of specialists integrating XDR-class products with network security or network monitoring (NDR) solutions – we will be happy to talk about Log4j mitigation methods adopted in your organization and share our thoughts.




