NIST Cybersecurity Framework – character depiction
The National Institute of Standards and Technology (NIST) the cybersecurity framework is a set of guidelines for private sector companies that must be followed to better prepare to identify, block, detect, respond, and remediate the effects of attacks. It is a set of best practices, standards and recommendations that helps an organization improve its cyber security measures.
The NIST framework aims to solve the problem of the lack of generally accepted standards when it comes to IT security. Today, there are big differences in the way companies use technology, communications, and policies to fight cybersecurity breaches. Cyber attacks are becoming more widespread and complex. Therefore the lack of a unified strategy among organizations makes defense much more difficult.
The different sets of cybersecurity toles (policies, guidelines, practices and technologies) pose another problem. Namely, organizations are unable to share information about attacks. The NIST framework aims to eliminate all of this. With a uniform set of rules, guidelines and standards, it is easier to exchange information between two companies therefore it is easier to find everyone on the same page.
It could be argued that anyone who uses a computer should think about NIST’s cyber security framework. It covers the entire organization. The IT department implements the technological layer, but it is the business representatives’ shoulders to implement the policies for safe work with data and the network. The IT security team cannot do without alone.
The structure of NIST is broken down into specific areas
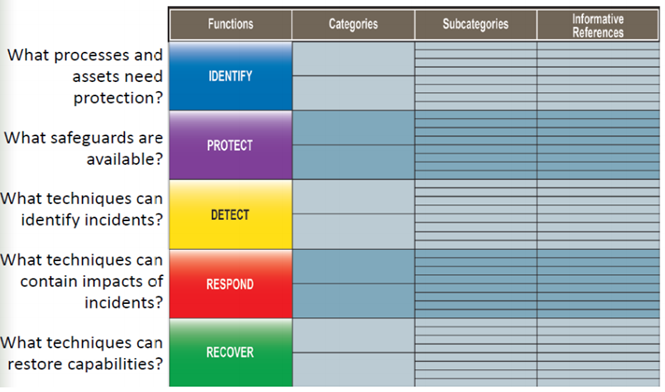
FRAMEWORK CORE
The core of the platform defines the actions that must be performed to achieve different cybersecurity outcomes.
It is broken down into four different components:
Functions – The 5 functions described in the NIST Cybersecurity Framework are identification, detection, protection, response, and recovery. These are your most basic cybersecurity tasks. Identify – Protect – Detect – Respond – Recover (IPDRR)
- Categories – For each of the five functions, there are categories that are specific challenges or tasks that you need to complete. For example, to protect your systems, you should implement software updates, install antivirus and anti-malware programs, and have an access control policy.
- Sub-categories – these are tasks or challenges related to each category. For example, when you deploy software (category) updates, you need to make sure that all Windows computers have automatic updates turned on.
- Informative References – these are documents/materials that describe in detail the specific tasks of users related to performing specific activities. For example, you should have a document that details how automatic updating is enabled for Windows computers.
IMPLEMENTATION TIERS
The NIST cybersecurity framework defines four levels of implementation. This would help you see what level of compliance you are at. The higher the level, the more compatible you are.
- Tier 1: Partial – cybersecurity is a coincidence, no structures, information sharing and cybersecurity awareness at the level of the entire organization.
- Tier 2: Risk Informed – the organization has basic cybersecurity procedures, implemented technologies and awareness at the organization level.
- Tier 3: Repeatable – cybersecurity awareness at all management levels, protection mechanisms based on risk analysis, the company actively shares information about cyber threats with the ecosystem.
- Tier 4: Adaptive – a dynamic approach to risk management that assumes constant monitoring and updating of its level. The implemented technologies usually use machine learning algorithms to proactively assess and mitigate risk.
PROFILES
The profiles under the NIST Cybersecurity Framework address both the current state of your organization’s cyber security measures and the plans you have to comply with the NIST Cybersecurity Framework.
This is based on an estimate based on the Core Framework of your:
- The current state of cybersecurity – Current Profile.
- Desired Cybersecurity Status – Target Profile.
And then, e.g. by analyzing the gaps between the above profiles, develop a transition strategy.
CURRENT PROFILE – cybersecurity activities – TARGET PROFILES
Profiles are also intended to help business managers see how each feature, category or subcategory can help the enterprise in general, thus providing visible benefits from adhering to the security framework.
The profiles are also intended to help business managers see how each feature, category or subcategory can help a business in general, thus providing visible benefits from following the NIST cybersecurity framework. They can be considered as a summary of everything the organization has done in terms of NIST Cybersecurity Framework.
If you are a private organization, you may not implement the NIST framework. There is no legal or regulatory obligation to do so. Implementing this also involves a significant investment, which is why some companies avoid fully implementing the framework in their own organizational structures. To help companies and public agencies implement its Cybersecurity Guidelines, NIST provides several resources on its website, such as FAQs, industry resources, case studies, and other tips.




