Vectra Cognito – simple and effective solution to protect Microsoft Office 365
Currently, Office 365 dominates the productivity space with over 250 million active users each month. For many of these users, Office 365 is the foundation of enterprise data sharing, communication, and storage, making it an incredibly rich data target. So it’s no surprise that accounts in Office 365 are currently the main vector of cloud security threats. As a result, the number of unwanted incidents via Office 365 is growing rapidly. What do attackers use and what information are they looking for? Why is it worth investing in Vectra Cognito? Meet our simple and effective solution for protecting Microsoft Office 365.
Attackers use authorized tools and services included in Office 365
Power Automate
Microsoft Power Automate allows users to create custom integrations and automated workflows between Office 365 applications. It is turned on by default and includes connectors for hundreds of third-party applications and services. The wide availability and ease of use of Power Automate also makes it a partially useful tool for attackers to organize living-off-land attacks and internal propagation.
eDiscovery
Microsoft eDiscovery is an electronic discovery tool that searches Office 365 applications and data and exports the results. It can be invaluable in the performance of governance & compliance tasks. Attackers use eDiscovery as an internal data recognition and exfiltration tool.
Oauth
OAuth is an open standard for access authentication. It is used by third party applications to authenticate users with the Office 365 sign-in services and associated user credentials.
One of the largest studies of Office 365 security in organizations was carried out by Vectra AI – a producer of NDR class solutions. This is not accidental, behaviors are now the main plane for identifying advanced threats, and the web is where you can see them most clearly.
Key findings from this study, which includes 4 million Office 365 accounts, include:
- 96% of customers have experienced lateral movements
- 71% of customers reported suspicious behavior with Office 365 Power Automate.
- 56% of customers showed suspicious eDiscovery behavior in Office 365.
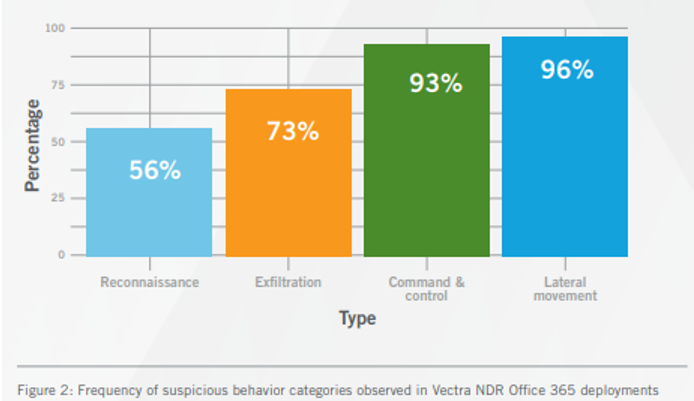
The most frequently identified activities included in the attacks on Office 365 are:
- Searching e-mails, chat history and files for passwords and sensitive data.
- Set up redirect rules to access a steady stream of email without logging back in.
- Use a trusted email communication channel to impersonate employees, customers or partners.
- Include malware or malicious links in documents that are used by many people.
- Stealing or storing files and data for ransom payment.
It is impossible not to notice that these are quite simple techniques, as the key phase is getting access itself.
| Vectra detection in Office 365 | MITRE ATT&CK framework | Associated attacker behavior |
| Risky exchange operation | • T1484 Group Policy Modification • T1098 Account Manipulation | Lateral movement An attacker is manipulating Microsoft Exchange to access a specific set of data or to enable continued attack progression. |
| Suspicious sign-on activity | • T1078 Valid Accounts | Command and control An adversary has stolen a valid account and is using it as part of an attack. |
| Suspicious Azure AD operation | • T1078 Valid Accounts | Lateral movement Attackers might be escalating privileges and performing administrator-level operations after a regular account takeover. |
| Suspicious Power Automate flow creation | • T1041 Exfiltration Over C2 Channel • T1008 Fallback Channels T1105 Ingress Tool Transfer • T1059 Command and Scripting Interpreter • T1020 Automated Exfiltration | Command and control An adversary has leveraged Power Automate as a persistence mechanism inside the environment. |
| Redundant access creation | • T1098 Account Manipulation | Command and control An adversary has provisioned access into a sensitive role to create redundant access into the network. |
| Suspicious SharePoint operation | • T1078 Valid Accounts • T1213 Data from Information Repositories | Lateral movement An attacker has located a SharePoint administrative account and is using it in pursuit of attack progression. |
| Unusual eDiscovery search | • T1119 Automated Collection • T1213 Data from Information Repositories • T1083 File and Directory Discovery | Internal reconnaissance An adversary has gained access to eDiscovery capabilities and is using it to perform internal reconnaissance across the environment. |
| Suspicious mail forwarding | • T1114 Email Collection | Data exfiltration An external attacker has established persistent access to the contents of a specific mailbox without having to maintain persistence by installing software. |
| Account manipulation | • T1098 Account Manipulation | Lateral movement An attacker has escalated the account’s Microsoft Exchange access rights to enable business email compromise or the collection of additional information to aid in the next step of the attack. |
| eDiscovery exfiltration | • T1048 Exfiltration Over Alternative Protocol | Data exfiltration An adversary has gained access to eDiscovery capabilities and is using that access to collect or exfiltrate data. |
Source: Vectra INDUSTRY REPORT: The 2020 Spotlight Report on Office 365
The main problems for today’s enterprises
The organisation’s main concern when it comes to managing Office 365 is that identifying user access fraud has been addressed using an approach that focuses on static policies which reveal threats as they occur, leaving little time for appropriate react.
This type of access monitoring only shows that the account is approved and used to access resources. It gives no insight into how or why resources are being used. Security teams need to have a detailed context of how individuals use their privileges known as privilege monitoring in SaaS applications such as Office 365. This translates into understanding how users access Office 365 resources and from where, but without looking at the entire data load to protect privacy.
It’s all about usage and behavior patterns, not static access. The importance of keeping a close eye on user access abuses cannot be overstated, given its prevalence in real-world attacks. Unfortunately, platforms such as Office 365 are so far a safe space for attackers’ internal movements, which makes it most important to focus on user access to accounts and services.
Therefore, an effective solution is Vectra Cognito, which detects and allows you to effectively respond to incidents in the cloud
The Vectra platform prevents data theft in the cloud, automatically by detecting threats and prioritizing them, thus improving your investigations.
In this case, for SaaS application protection, Vectra’s methodology, already proven in data centers and corporate networks, is used.
The Cognito solution combines expert knowledge and artificial intelligence to spot attacks in real time and enable immediate action or to automate the response to a threat.
It takes literally a few minutes to implement this solution. Cognito Detect integrates seamlessly with the existing Office 365 environment because it doesn’t need any changes or agent installations. Just plug in the instance and Vectra will immediately start detecting any suspicious events.
The Vectra Cognito platform allows you to get a perfect situational picture of the entire IT infrastructure, both physical and cloud based. Without increasing the workload of the teams responsible for IT security we enable uncovering dangerous events.
Stay ahead of hackers and respond quickly to hidden threats. Vectra integrates with existing security tools such as SIEM and complements specific tools such as SOAR or EDR.
If you are interested, please see the entire Vectra report.
And we invite you to a dedicated presentation with our specialists!




