Vectra AI – time-saving detection & reaction
Vectra provides visibility for security analysts, prioritizes alerts, limits information to only necessary, and then initiates a response directly or indirectly – through integration. It is believed that every security solution is supposed to do this in theory. The IDC report shows that Vectra has done this in practice. Read further to see what conclusions can be drawn from this.
Currently, the corporate network extends horizontally, without granular access&authentication policies and covers direct access to SaaS applications in the data center and cloud. The size of the traffic makes it difficult to detect suspicious network behavior such as access to new domains, strange port activity or protocols. Vectra analysts are investigating how network and cloud metadata can be selected and enriched by enabling real insight into the network, hosts, and accounts to detect subtle but unchanging behavior by attackers. Like scratches on the surface of water that made by something flowing under the surface.
In this article, we provide an IDC report on the use of the Vectra system.
IDC, encouraged by the raise in customer interest towards NDR solutions, spoke to nine large (> 24,000 users;> 19 bil.$ Revenue) organizations operating in a variety of (international) locations and industry sectors. Every one of them uses Vectra’s Cognito platforms to secure their IT resources. What are the findings?
What is Vectra?
Vectra uses sensor-based technology to extract metadata from network traffic or cloud logs, including SaaS and IaaS, data center hypervisors and IoT devices, analyze them and detect threats. The leading product of Vectra is Cognito – a platform for detection and response to network events, and Cognito Detect for Office 365.
Cognito uses a combination of supervised and unsupervised machine learning. It is supported by combination of over 40 supervised detection models to detect attackers behavior. And unsupervised learning uses 11 machine learning algorithms to help define reference groups, statistical baselines of end user network behaviors and models designed to mimic and predict the attacker’s actions.
Vectra provides visibility to security analysts, prioritizes alerts, presents only research-supporting information, and then directly or indirectly through integration initiates the right response. Security tools are believed to do this in theory. IDC said Vectra did this in practice. Conclusions?
Vectra customers are listing the benefits of security improvements through threat detection and prioritization based on artificial intelligence (AI). All the organizations interviewed use Cognito Detect, about half of which use Cognito Stream and Cognito Recall.
IDC analysts started by analyzing the current situation and identified 3 main trends in cybersecurity – regardless of sector or geographic location:
- Shortage of security analysts.
- Point-based IT Security solutions do not provide context or prioritize alerts and do not provide a single point of management.
- The sudden digital transformation caused by COVID-19 has changed the network fundamentally and irreversibly.
To protect effectively, it’s worth noting that the cloud, data, files, workflows, and devices all share one common point – the network. A properly understood network reveals which hosts and accounts are most vulnerable, whether there is an attacker and attack vector, and what to do about it.
At the same time, the study participants also identified other challenges that determined the expansion of the IT security infrastructure with NDR class solutions. The main purchasing motive was the conviction that the organization lacks key capabilities in identifying and mitigating threats to the security of their business operations.
First impressions of VECTRA’s COGNITO
- Unparalleled reporting and analytical capabilities – supervised and unsupervised Machine Learning, the number of algorithms supported by it and the way they are implemented is the main distinguishing feature of Vectra technology.
- The most advanced threat detection capabilities, effective in ensuring compliance with regulations – one of the few solutions that combines excellent anomaly detection with a filter that correlates detections with possible violations of regulations binding a company.
- The ability to see the value during the tests (POC) – Vectra is a good solution not only in PowerPoint. Given its complexity, the evaluation process usually includes PoC – and let’s say customers aren’t disappointed with what they see.
For the most part of Vectra, the Cognito platform was implemented as an additional solution to its security environments, which already included various third-party solutions such as Next Gen Firewall, EDR or SIEM.
The organizations interviewed indicated key benefits in several areas
1. Risk mitigation and operational efficiency
Reduced risk means lower costs and process delays associated with security breaches and unplanned downtime, as well as long-term reputational losses. It is worth noting that the average loss per incident is almost $ 1 million per hour ($ 884,000) in lost revenue and the effort spent detecting and mitigating the incident. The study participants uniformly linked Vectra Cognito with a significant reduction in the risk of such events.
- Speed of handling alerts – one of the key indicators that should improve after the implementation of NDR. Thanks to the workflows and prioritization built into Cognito, Vectra’s customers notice a significant improvement in the first months of use.
- Improved ability to identify network intrusions – here understood as an improvement in penetration testing results after the implementation of Cognito. 100% of the respondents stated an improvement in this area.
- Faster identification of events and configurations – one of the most important cybersecurity features is identifying faulty configurations and bogus systems that should not be online. Thanks to Vectra’s solution – present at its customers premises and clouds.
2. Risk reduction and increased productivity
Study participants not only significantly reduced their spending on business risk mitigation. IDC calculates that interviewed customers will earn an average of $ 1.31 million ($ 54,500 per 1,000 users) through reduced risk management, incident handling, and system unavailability costs.
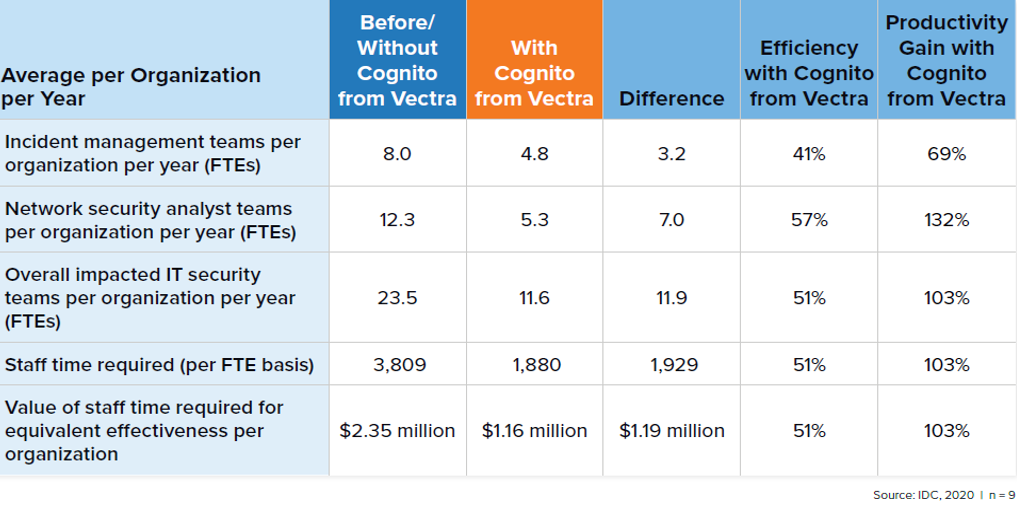
3. Efficiency of the security team and saving security costs
IDC estimates that the increase in the productivity of IT security workers along with the reduction of the cost of operating the security infrastructure may be worth an average of $ 1.31 million ($ 54,200 per 1,000 users).
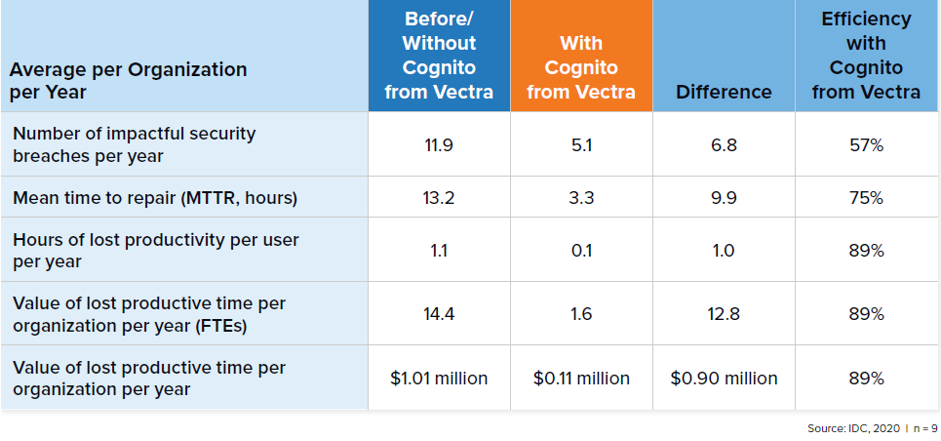
4. Performance of the security team – KPI’s
According to a report, Cognito significantly improves KPIs connected to security team’s operations. The effectiveness of security teams comes from using Cognito for getting up-to-date and relevant information about potential threats based on AI and data science analysis.
Impact of Vectra Cognito on security team statistics
5. Cost effectiveness & return on investment
The implementation of Cognito allows to minimize the total cost of operations of the IT security department.
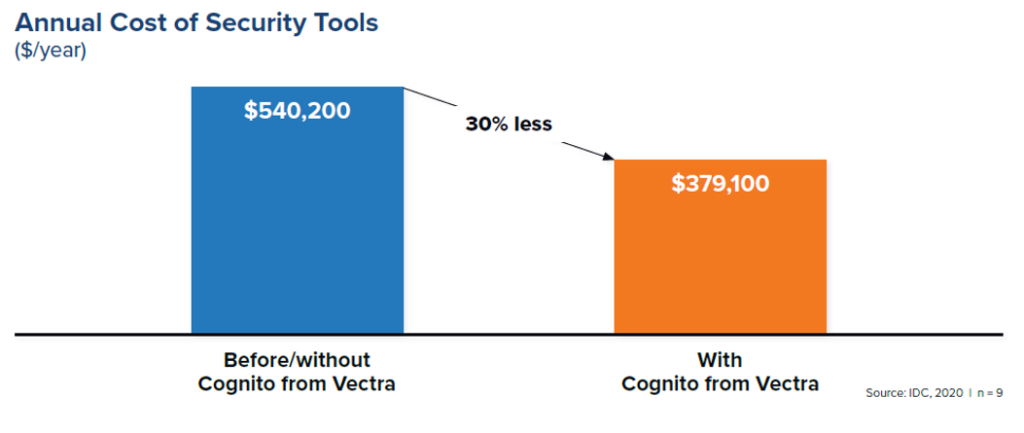
The general chart above shows the reduction of the costs of maintaining and using cybersecurity systems, including: purchase and renewal costs, costs of IT security employees, management costs and direct costs of the entire IT related to the maintenance of the systems. By improving the efficiency of processes, enterprises find space for better budget usage and enjoy a return on investment of 360% over 3 years.
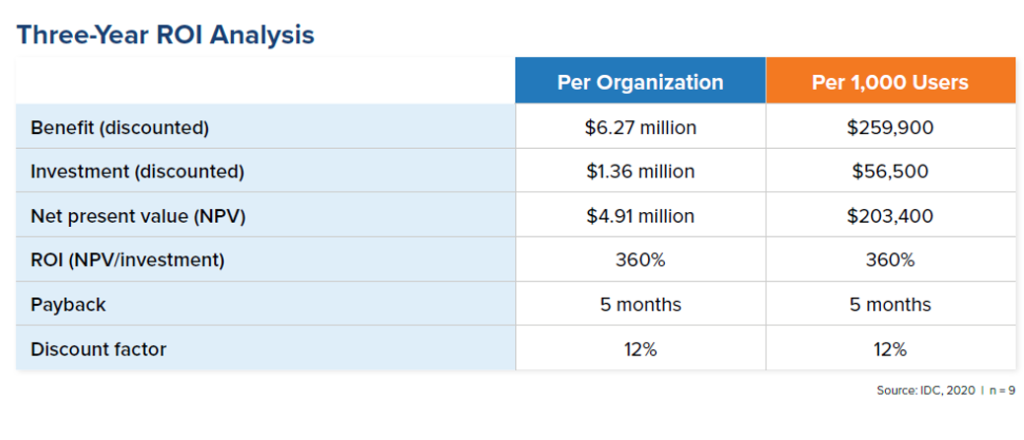
During the interviews, IDC analysts came to surprising conclusions. Namely, the purpose of the cybersecurity tool is not to search for the so-called Indicators of Compromise, i.e. signs that the system is infected. Because this so-called “system” contains a relatively unstable network component that adapts to new users, background updates, shadow IT, software and applications, and conditions such as load balancing, power, downtime. Each new parameter is an additional noise and disturbance of the tool operation. The expertly designed solution not only finds evidence of an attack, but also provides the analyst with tools to investigate the event. It does not change the fact that the network is an excellent control pane. Measurements of e.g. session entropy, HTTP tunnels and suspicious connections to non-standard ports are just some of the things Vectra look at.
The primary and ultimate goal of cybersecurity tools is to combine trade-off indicators into a true version of events, determine the likelihood of an incoming or ongoing attack, and trigger an appropriate response. Cognito by Vectra has and carries out all these elements. We encourage you to read the full report below (LINK BELOW):
Source: IDC, The Business Value of Cognito Network Detection and Response from Vectra




