SOAR – invaluable support from the Incident Reponse teams
Since 2018, Palo Alto, which has its fair share of SOARs through its xCortex platform, has published the State of SOAR report, containing facts about use of the technology by IT security professionals from various industries. The authors ask them about their incident response practices, as well as their insights on the current and future use of orchestration, automation and response (SOAR) as it relates to their operations. In this article, we present some of the more interesting insights behind the report.
Let’s start with a reminder – SOAR – Security Orchestration Automation & Response. This term is used to describe three system capabilities:
- threat and vulnerability management
- response to security incidents
- automation of security operations.
SOAR enables companies to collect threat-related data from a variety of (internal and external) sources and automate responses to low-level threats. According to Gartner, SOAR allows for a 5%-10% improvement in the daily analysis capabilities of each malware sample or alert selection.
According to a report presenting data from 2020, security analysts are dealing with the increasing complexity of attacks, not a revolutionary finding… What is overwhelming is that analysts currently have to track an average of 6.8 sources of threat information and manually handle most alerts.
“IR processes arise across a wide range of systems, and the resulting workflow crosses many organizational barriers.”
If you are considering implementing a SOAR solution – those who already have a SOAR tool on board – most often use it to*:
- detection and Response – 45%
- vulnerability prioritization – 37%
- compliance monitoring – 30%
- security audits – 30%
*The percentage in the above represents how many percent unanimously identified the use case as being used in SOAR at that point in time
Unfortunately, COVID-19 made things worse. Forty percent of respondents believe the pandemic is causing more resource constraints. This is for three main reasons – related to remote work:
- the complexity of hacking campaigns has increased
- the number of attacks has increased (distributed networks are easier to attack)
- security analysts are generally not responding well to both work at home and their users working from home
Fortunately, the security analysts surveyed are clear about what they need to do their jobs more efficiently. The main trend is the aforementioned automation of response to low-level threats – alert overload is too high.
Key initiatives, tied to Security Orchestration, Automation & Response capabilities are:
- Increase automated processes – to better allocate analyst attention and reduce manual errors. 65% of respondents placed incident response automation as a priority in 2021.
- Integration of SOC tools with third-party systems – they can easily connect to other Incident Reponse departments and processes. 30% of respondents say they want a common platform for cross-functional team response.
- More playbooks – including third-party and community-created, so they can leverage the proven expertise of other teams. 78% of respondents would like to see a common framework and community for playbook sharing and integration.
Technical priorities are reflected in the company’s IT strategy. Palo Alto Networks shows that the rise in demand for IT security automation correlates with the use of cloud, IoT and interestingly, offensive cybersecurity strategies – Red Teaming. Below we show the use-cases that respondents most frequently identified as ones where SOAR would be applicable due to automated responses based on knowledge from multiple sources.
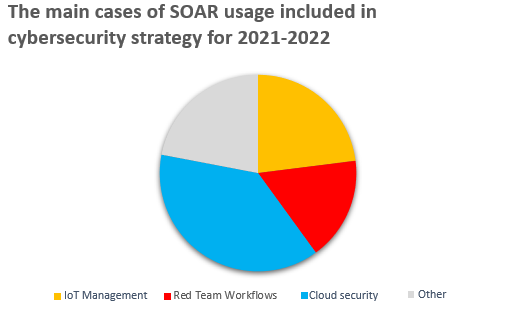
Brief conclusions on the state of technology in the enterprises surveyed – 43% of those surveyed said they plan to increase spending on SOAR tools in 2021. The COVID-19 pandemic prompted 47% of respondents to increase their use of SOAR. As you can see, automation is not just the domain of Industry 4.0.
Summing up – SOC teams need to reduce alert fatigue. And the sudden increase in dispersion associated with the adoption of cloud services and the avalanche of events generated by IoT certainly doesn’t help. What’s needed is a tool that can reduce alerts or speed up the process of managing them. SOAR offers a solution to many of these challenges. Technology helps SOC teams save time, speed up segregation and reduce the number of steps in incident response processes.
We also encourage you to read the full Palo Alto report on the website