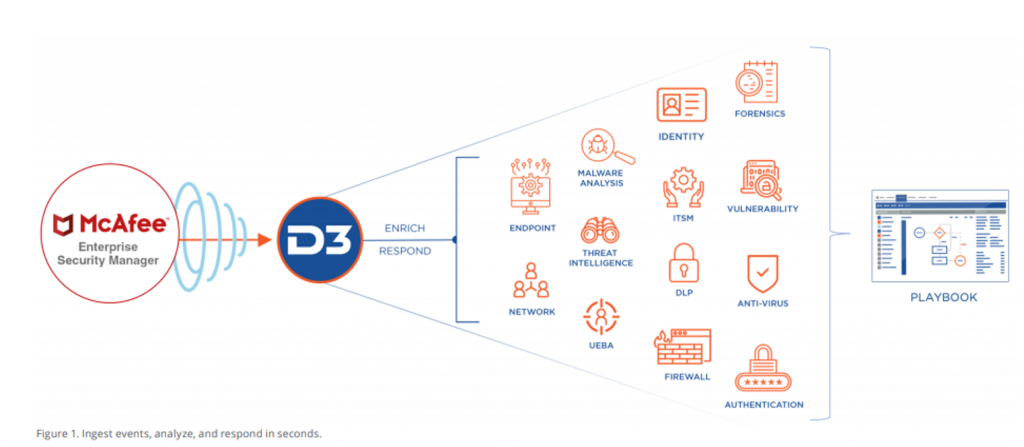
SOAR – a perfect complement to SIEM
In today’s world, information is power. Especially in the world of cybersecurity. Information delivered on time can prevent financial loss by blocking data leakage or even save human life – preventing service downtime, e.g. automatic drug dosing. Managers who are victims of cyber attacks ask themselves one question – what could we do if we had known about it earlier?
This translates into pressure on cybersecurity teams. More point solutions – whose alerts need to be correlated and patterned. More alerts. Limited automation possibilities. Add pressure from business. For shorter incident response times. For less false-positives. For a shorter time to detect an attacker inside the network. To reduce ARO – Annual Rate of Occurrence – for each type of attack. Have you had enough? Not only you.
Due to the many sources of information and the difficulty of correlation, organizations with SOC (Security Operation Center) implement SIEM solutions – Security Information & Event Management. SIEM uses correlation rules and statistical algorithms to extract useful information from events and logs.
The key features of the SIEM security solution are:
- Near real-time visibility: SIEM uses visual consoles as dashboards and provides an overall view of the security system.
- Data Consolidation: manages log streams from various sources.
- Event correlation: adds context to the raw data.
- Automatic alerts of security events: Analyzes intrusion rates and sends alerts by notifying you of events in real time.
To show the scale of events managed by SIEM – Gartner considers a SIEM small if it has up to 300 log sourcesand generating 1500 events per second. Large SIEMs handle thousands of event sources, generating over 25,000 events per second. The main skill of SIEM is to filter all data and prioritize security alerts.
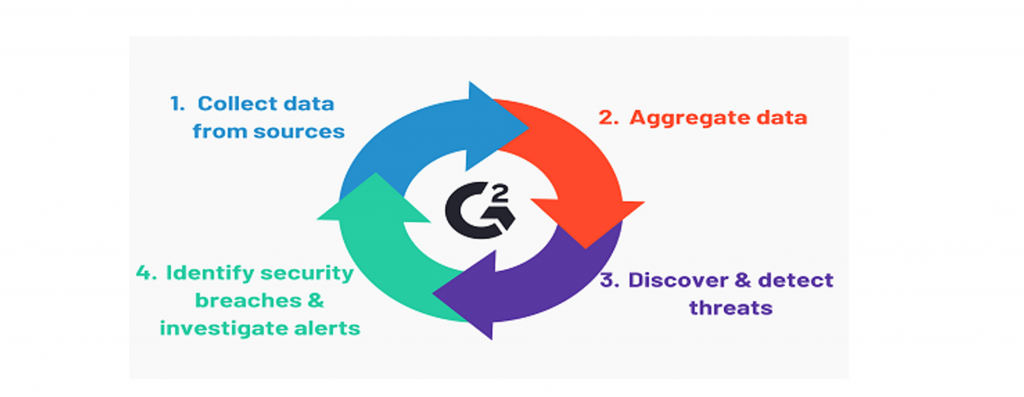
Figure 1. SIEM workflow
Does the SIEM implementation solves the problems of modern SOC?
Well… no. Different sources give different values, by the law of the mean we can say that about 40% of security alerts are not investigated. Divergent tools generate thousands of alerts and force SOC analysts to ignore them or chase false-positves. According to Gartner, 99% of the vulnerabilities used in the attacks have been known for at least a year before the attack. SIEM tools usually require regular tuning to continually catch and distinguish anomalies and normal activity. The need for regular fine-tuning leads to security analysts and engineers wasting valuable time making the tool work instead of controlling the constant flow of data.
The business problem is not zero-days, it is the lack of SOC learning from the tactics and techniques seen both on the Internet and in their own environment.
The answer to this problem is the use ofSOAR – Security Orchestration Automation & Response. The term is used to describe the three capabilities of the system – threat and vulnerability management, security incident response, and security operation automation. SOAR enables companies to collect threat-related data from a variety of sources and
At this stage, a frequently asked question from SOC representatives is: “We already have a SIEM to aggregate and monitor security alerts. Isn’t that basically what SOAR does? “
SIEM and SOAR deployed simultaneously do not lead to unnecessary redundancy, despite some superficial similarities. In fact, SOAR is the perfect complement to SIEM, extending SIEM’s capabilities for effective analysis, investigation and response to alerts – especially low-level alerts, which make up the vast majority of alerts. SIEM is an excellent source of alerts, with its ability to aggregate and detect anomalies in activity.
Having a SOAR platform to escalate important alerts gives SIEM security teams the ability to optimize and automate their workflows, including:
- enriching alerts with contextual information about threats and other data,
- creating scenarios specific to incidents based on automation,
- organized activities throughout the security environment,
- comprehensive dashboards and reporting.
We can consider it as a second layer of automation – allowing us to obtain next-generation SOC. We are talking here about a cutting-edge approach to the SecOps concept – understood as a platform for facilitating cooperation between IT security teams and operational teams, and the integration of technologies and processes that they use to ensure the security of systems and data.
Both SIEM and SOAR aim to improve the life of the security team, from the analyst to the CISO, by increasing the effectiveness of the SOC and reducing the vulnerability of the organization. While data collection is critical, SIEM solutions generate more alerts than SecOps teams can handle effectively. Adding SOAR as a layer enables the security team to deal quickly and efficiently with large numbers of alerts.