MalOps by Cybereason – Capture malicious processes, not alerts
We often repeat that the company’s “business” should not treat security departments as police – rather as a secret service-style security department. However, there is one thing in common – both of these organs are either passive or reactive. They respond to an attack or create circumstances that make it difficult, do not take action until the attack actually occurs.
And for attackers the properly conducted reconnaissance allows to access the network in a few minutes, and one compromised account is enough for a bad actor to gain an initial foothold. Once access is granted, it may take weeks or even months for any damage to be done. This is because the enemy will try to gain more control by learning about the network structure and identifying security weaknesses in the compromised network. The attacker moves slowly on purpose, employing various techniques to trick the defender, avoid detection, stay online, and achieve the ultimate goal.
Therefore, security incidents should be seen in the context of what else is happening in the entire IT environment. Cybereason approaches security incidents from the perspective of operations as a set of related activities. They define the above as MalOp: the time frame and set of actions taken by hackers from penetrating the network to achieving their operational goals.
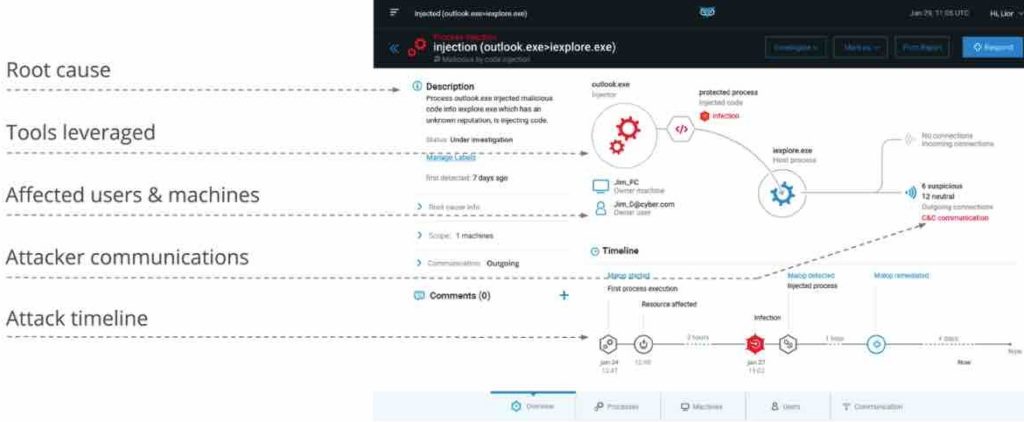
Below is an example of MalOp in the Cybereason console:
- When Cybereason finds any unusual data that is relevant to the detection process, it is flagged as evidence – which can be compared to a security analyst’s gut feeling.
- As soon as activity marked as evidence shows signs of turning into suspicion (the term Cybereason means the incident looks strange but is not a full-scale attack), the system links the suspicions together until a complete attack history is formed. This story shows the schedule of the attack, its root cause, the affected computers and the users affected.
Treating each suspicion as part of a larger malicious operation rather than a single event reduces the number of threats the security team has to investigate. Fewer threats to investigate reduce the chances of encountering false positives.
Below we present a demo in which we detect MalOps using highly destructive wipers called WhisperGate and HermeticWiper – part of the Russian cyber attack on Ukraine
WhisperGate masquerades as ransomware and paralyzed many Ukrainian organizations. It is delivered through a multi-stage infection chain with two main malware components:
- Stage 1: A Master Boot Record (MBR) lock used to overwrite the operating system’s MBR, effectively preventing the operating system from loading successfully
- Stage 2: Disk wiping used to clean and shred files on the target computer.
Although the software has not been attributed to a particular Russian APT group, Ukrainian officials have publicly attributed the attack to Russia as a potential step to “prepare the ground” for an upcoming military operation. Cybereason Anti-Ransomware and Anti-MBR technology on Cybereason XDR corruption detects and prevents WhisperGate Wiper as well as all other ransomware and Wiper strains.
DEMO:
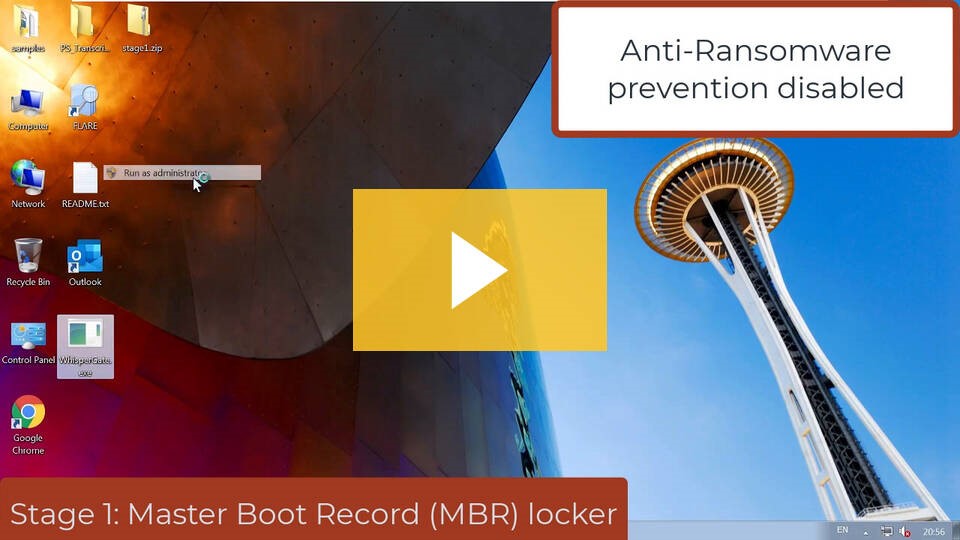
Cybereason vs. WhisperGate and HermeticWiper
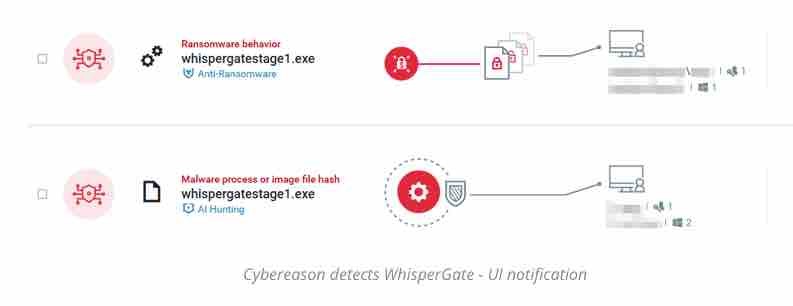
In Cybereason, ransomware protection can be achieved in two steps:
- Enable Anti-Ransomware in Cybereason NGAV: Set Cybereason Anti-Ransomware protection mode to Prevent with MBR protection
- Enable Anti-Malware in Cybereason NGAV: Set Cybereason Anti-Malware to Prevention and set the detection mode to Moderate or higher
It is worth adding that, according to the MITRE – Cyberason is characterized by the highest detectability of attacks:
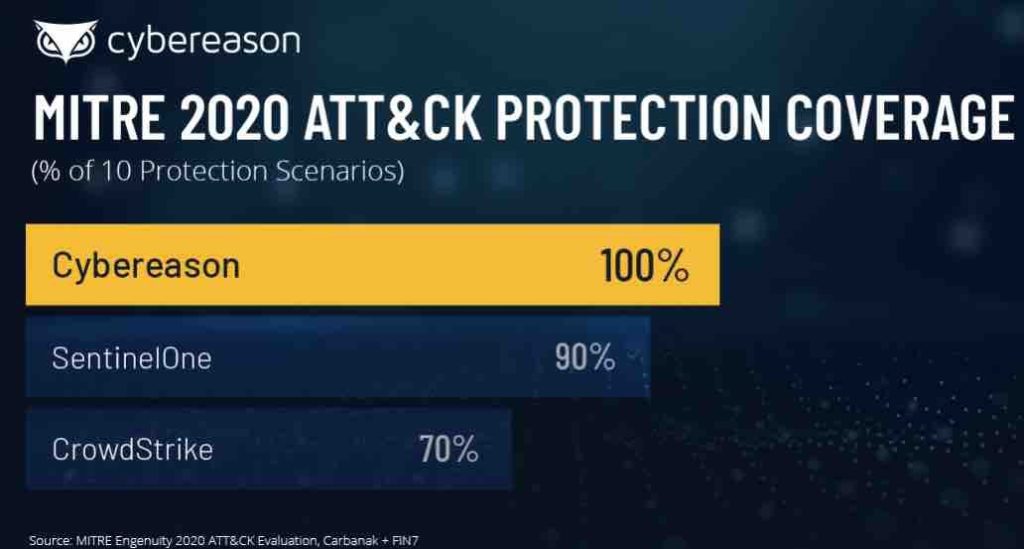
If you would like to match Cybereason detections to campaigns or scenarios seen in your industry – we are open to discuss on the meeting. Security does not like too much noise!




