ISO27001 – introducing Annex A!
Annex A to ISO 27001 is probably the most famous of all ISO standards – it provides a basic information security risk management tool: a list of security checkpoints (or safeguards) to be applied to improve the security of information assets. This article provides an understanding of the structure of Annex A and its relationship to the main part of ISO 27001 and ISO 27002.
The best way to understand Annex A is to think of it as a directory of information security controls from which you can choose – from the 114 control points listed under the 14 domains in the Annex ]. You can use them in two main ways:
- Designing the company’s security strategy – by selecting those control points that apply to your organization. Let’s call this the apriori approach.
- Assessment of the organization’s readiness for the information security management process – relating the security policies and technologies to the individual control points in Annex A. Let’s call this approach a posteriori – because we are assessing the already implemented security strategy.
This list of ISO 27001 control points is included in the 14 domains described in Annex A. Contrary to appearances, not all of them are IT-oriented – here is a summary that shows what the control points focus on. These are the sections:
- related to organizational issues: A.5, A.6., A.8, A.15
- on human resources: A.7
- related to IT: A.9, A.10, A.12, A.13. A.14, A.16, A.17
- regarding physical security: A.11
- concerning legal issues: A.18
In percentages it looks like this:
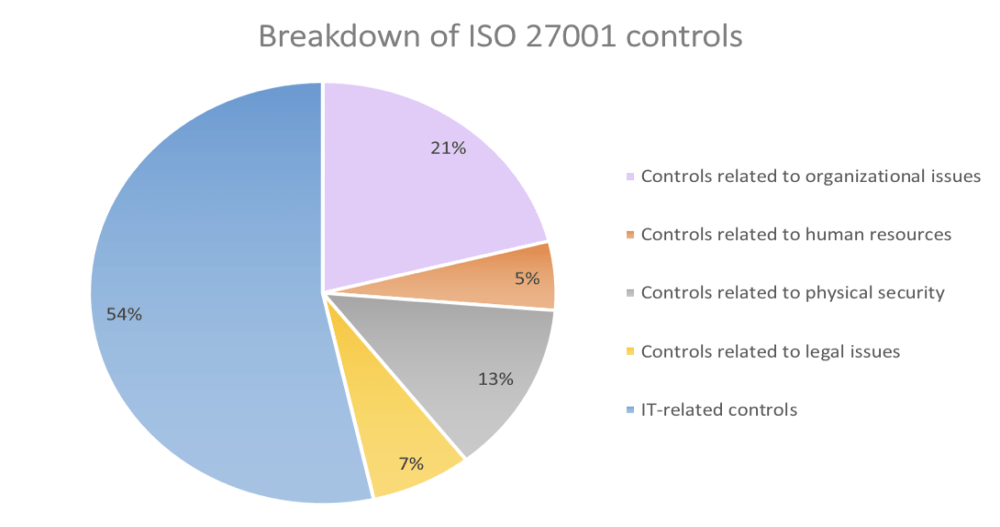
Looking at the chart above, we can see that over 50% are control points related to your IT infrastructure. This is why cybersecurity specialists strongly rely on the ISO 27001 standard.
Below we present the extensions of 14 ISO 27001 domains broken down into the sections identified above:
IT RELATED DOMAINS:
- A.9 Access control – controls for managing the access rights of users, systems and applications, and managing user responsibilities
- A.10 Cryptography – Controls related to encryption and key management
- A.12 Operational security – many controls related to IT production management: change management, performance management, malware, backup, login, monitoring, installation, vulnerabilities etc.
- A.13 Communication security – controls related to network security, segregation, network services, information transfer, messaging etc.
- A.14 System Acquisition, Development, and Maintenance – Controls that define security requirements and security in development and support processes
- A.16 Information security incident management – controls for reporting incidents and vulnerabilities, determining accountability, response procedures and gathering evidence
- A.17 Information security aspects of business continuity management – controls that require business continuity planning, procedures, verification and review, and IT redundancy
DOMAINS RELATED TO ORGANIZATIONAL ISSUES:
- A.5 Information Security Policies – Controls of the way policies are written and reviewed
- A.6 Organization of information security – control of assignment of duties; it also covers the control of mobile devices and teleworking
- A.8 Asset management – controls related to asset inventory and acceptable use; also for information classification and media handling
- A.15 Supplier relationships – Checks on what to include in contracts and how to monitor suppliers
DOMAINS RELATED TO LEGAL ISSUES:
- A.18 Compliance – controls that require identification of applicable laws and regulations, intellectual property protection, personal data protection, and information security reviews
DOMAINS RELATING TO HUMAN RESOURCES:
- A.7 Human Resource Security – Pre-Employment, During, and Post-Employment Controls
DOMAINS RELATED TO PHYSICAL SECURITY ISSUES:
- A.11 Physical and environmental security – controls to identify safe areas, entry controls, hazard protection, equipment security, safe disposal, clean desk and clean screen policy, etc.
These domains contain 114 security checkpoints – which must be implemented to ensure information security – and organize them into a system. As a reminder – an Information Security Management System (ISMS) is a set of rules that a company must establish in order to:
- identify stakeholders and their expectations towards the company in terms of information security
- identify the risks to the information
- define controls (safeguards) and other mitigation methods to meet the identified expectations and deal with the risk
- set clear goals for what to achieve with information security
- implement all controls and other risk management methods
- continuously measure whether implemented controls operate as expected
- make continuous improvements to make the entire ISMS run better
As a summary, it is worth adding that the primary goal of ISO 27001 is to protect three aspects of information:
- Confidentiality: Only authorized persons have the right to access information.
- Integrity: Only authorized persons can change information.
- Availability: information must be available to authorized persons whenever needed.
And it is through the prism of these three aspects that we should look at the implemented security control points.

