Increase in malware attacks revealed by the McAfee report
This year, reports of all kinds focus on the unprecedented circumstances of 2020. The challenges posed by the global COVID-19 pandemic in the area of cybersecurity include vulnerabilities exploited on an unprecedented scale, problems with the safe adoption of remote work and bandwidth problems in supporting remote connections to a central location. Most cybersecurity vendors publish reports and a variety of content to help professionals understand the spectrum of current threats. In our opinion, one of the publications that deserves attention due to the always up-to-date subject matter and impressive resources of knowledge – billions of data-points that provide data to laboratories every day – is the McAffee Labs Threats Report.
The second quarter of 2020 is the time of the most severe lockdown and burden on the IT infrastructure. This resulted in a significant increase in the statistics of attacks using malware.
- McAfee Labs saw 419 threats per minute in the second quarter of 2020, an increase of almost 12% from the previous year.
- 117% increase in new PowerShell malware compared to Q1, including Donoff PowerShell.
- The number of new binaries with malicious signatures increased by 25% compared to the previous quarter.
- New miner malware grew 25% over the previous quarter.
These are just a few selected examples of how criminals reacted to the unplanned virtualization of work in organizations around the world. Interestingly, the growth of cryptomining software – after all, the remote work environment potentially reduces the computing resources that are “borrowed” by the excavator.
The statistics of the malware executing PowerShell scripts are also worrying:
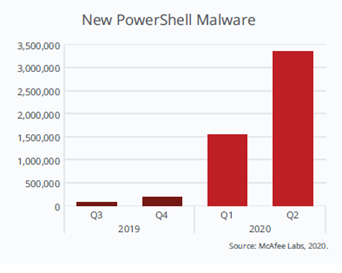
Due to the overlapping trends in the increase in the number of attacks and adaptation of cloud technologies, following the good practice of diversification – the largest organizations opted for a multi-cloud approach.
McAfee specialists identify 3 main trends for this type of IT infrastructure deployment:
- There is no one-size-fits-all hybrid environment model – organizations have different IT risks, needs, and software vulnerabilities.
- Zero-Trust Architecture – that is, multi-level authentication of the user at the points of “contact” with individual systems, will continue to evolve.
- Data protection policies need to be unified between on-prem and cloud-based data policies. Conditional and contextual access to data is critical to the full performance of an organization.
To show this issue from the bottom up, the report includes descriptions of malware campaigns and exploited vulnerabilities observed this year. This allows for a holistic view of cybersecurity challenges in this period, at least in several areas:
Cloud configuration errors – the configuration of the cloud environment is always the responsibility of the administrator. Providers have no control over the way you use their service. They provide “only” templates for personalization. All cloud service providers provide a resource credential management feature. McAfee presents an example of an attack on AWS, where this feature is called Instance Metadata Service (IMDS) and stores information about the instance, its network, and computing resources. The presented example shows how to access a private S3 Bucket through a reverse proxy that connects the publicly available application dashboard and its private resources, just using IMDS.
Robots, the final frontier – is a case of analysis of a global brand’s conference robot, which is gradually becoming the “future of communication” for corporate.

Analysis of the software’s source code reveals four separate CVE vulnerabilities, which, after exploitation, allow you to eavesdrop on video calls conducted through temi, intercept conversations directed to another user, and even remotely operate the temi – all without authentication. A positive accent of the whole project is the reaction of the robot manufacturer, which was involved in measures to mitigate vulnerabilities.
Malbus in The ONE STORE – a find mainly related to the Asian market, a new version of Malbus, previously found mainly on Google Play, was found in the South Korean ONE Store. Since the problem concerns distant lands – we will limit ourselves to presenting the diagram from the report:

Critical vulnerabilities found in Treck products – especially in their netoworking stack modules. There is an official statement on the company’s website listing the identified vulnerabilities. If you are using Treck equipment, please read: https://treck.com/vulnerability-response-information/.
Specific advice is valuable, including:
- Immediately rollout of updates published by the manufacturer after the CVE discovery.
- Introducing the least privilege principle for Treck devices – it is worth mentioning that least privilege is generally a good practice.
- Identification and isolation of devices outside the protected area of the corporate network.
- Use DNS caching along with DNS-over-HTTPS for searches.
- Increased network monitoring for non-standard IPs trying to establish connections.
One Drive Phishing – the number of attempts to obtain access data from Microsoft OneDrive users is growing. Fake e-mails from hackers pretending to be representatives of governmental, consulting or charity organizations are crafted to interest the user with new information on COVID-19 regulation … and to steal OneDrive credentials – username and password. McAfee experts rightly point out that the link indicates to users a domain other than Microsoft.
The user should be aware that the OneDrive login page will never be hosted on a domain other than Microsoft. It’s a huge red flag.
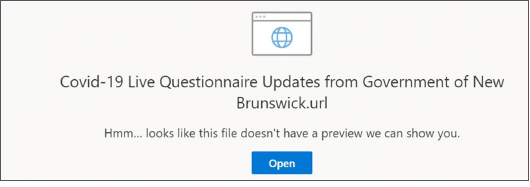
We have made every effort to include the key points of the report here, but for technical details, it is worth reading McAffee’s original reading. Especially due to the charts and data aggregations illustrating the state of cybersecurity in 2020.
We also include a list of valuable resources that can be used in daily IT security research:
- McAfee COVID-19 Dashboard – an observation panel for cyber threats taking advantage of the COVID19 pandemic.
- MVISION Insights Preview Dashboard – a business intelligence sample for McAfee cybersecurity.
- McAfee Threat Center – a comprehensive database of threats detected by the manufacturer.




