A step to the left on the attack timeline – how to prevent instead of treat
The traditional Indicators of Compromise (IOC) model assumes the recognition and correlation of malicious activities. If only as the basis for many of the action scenarios written into the SIEM – and possibly automatically mitigated by SOAR. However, the after-the-fact nature of IoC is a major limitation. These are documentation artifacts (file digest, IP address reputation, known bad URLs, memory footprint, etc.) based on an isolated action after it has occurred. Still, all too often their a 1:1 mapping where the IOC triggers an alert which is then reviewed by a Security Operations Center analyst to review or take action on potential clients to overload alerts.
Assuming security teams are able to handle verifying the authenticity of aleru…
- What is the lifespan of an IOC?
- How and when does a threat expire?
- How much “noise” occurs in threat intelligence data feeds?
At a time when your corporate “network” now consists of thousands of “one employee branches,” users are the new frontier, and data gravity has changed the approach to information protection. In this reality, Indicators of Compromise simply fail.
An organization that has found an answer to this change is Forcepoint – with its pioneering introduction of Indicators of Behaviour. An IOB recognizes how a user, device or account behaves. Forcepoint has designed dozens of IOBs with the express purpose of addressing the shortcomings of IoC. With IOBs, both context and timeline (the killchain equivalent) are key. IOBs focus on understanding the context of how your employees interact with your organization’s data and systems over time in a much broader way.
In their case, context means, for example, understanding typical:
1. User behavior.
2. Timeframes.
3. The applications used.
4. The actions they take.
5. The results he is trying to achieve.
Risk assessment is key, and controlling and monitoring access to applications and data is only part of that. IOBs also consider activities in the context of each other to arrive at an overall risk score. Typical employee behaviors, such as accessing approved applications and sharing data, will not negatively impact your risk score. However, risky behaviors such as taking screenshots of confidential documents, sharing them in a zoom session, saving them to a USB key or cloud storage service, or printing the same important documents at home can negatively impact an individual’s score.
The key to IOB effectiveness is an engine that counts individual user risk – something Forcepoint customers are familiar with from DLP (Incident Risk Ranking). Each IOB defines a baseline risk contribution along with intensity over time, and depending on further context, the risk contribution can go up or down.
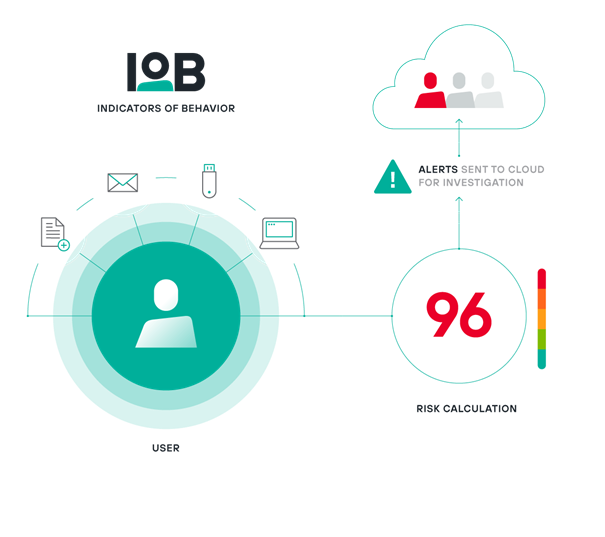
IOBs enable the transition from reactive to proactive reality. The dynamic risk assessments they provide allow security leaders to anticipate malicious activity such as data deletion, broken user credentials or other insider threats. Most importantly, they help security teams stay on the breach side – not the leak side.